
Cybersecurity in the era of digital progress, where data flow is steadily increasing and securing information systems is an issue, is becoming extremely relevant. Cyber threats are constantly evolving, requiring new, more advanced technological solutions. This article will look at advanced security technologies that are key in preserving data confidentiality, integrity, and availability in 2024.
Artificial Intelligence (AI) and Machine Learning (ML) in Cybersecurity

AI tools are evolving rapidly and uncontrollably, and cyber criminals are taking advantage. They have already learned how to use generative AI to create malicious code for automated malware attacks and how to use text, video, and image generation tools for phishing and social engineering practices.
However, cybersecurity experts are also implementing AI tools – algorithms that help automatically detect threats in real-time, identify anomalous behavior and fake generated content, and implement smart authentication and automated threat response mechanisms.
Zero Trust Architecture
Building a zero-trust architecture is a complex and ongoing process. In 2024, organizations will not apply all zero-trust principles or implement them all at once. They will start implementing such an architecture with small steps: identify and classify all the resources in the organization, implement effective user verification mechanisms, and start granting users only the privileges they need now.
Quantum-Safe Cryptography
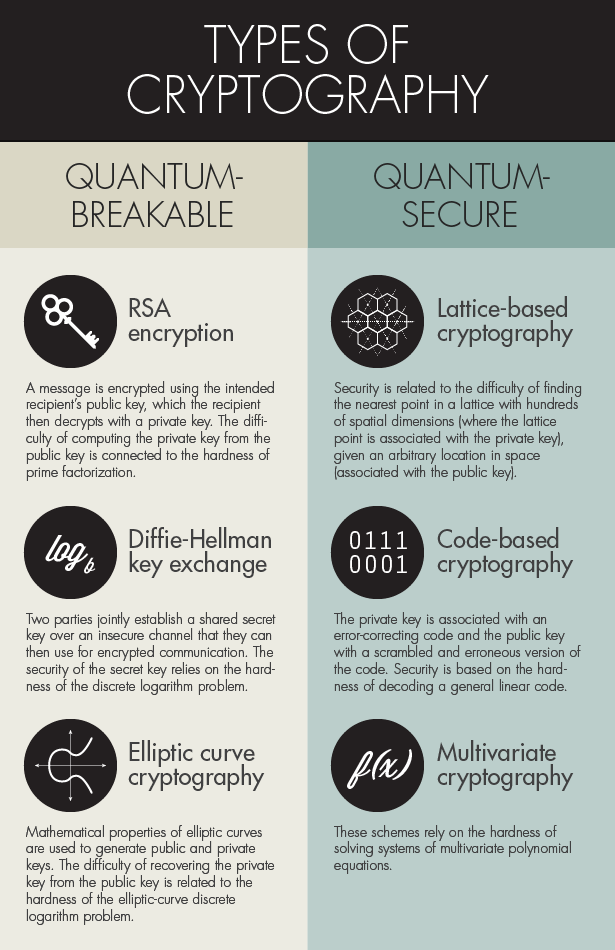
With the development of quantum computing, a new perspective on cryptography has emerged. Quantum-safe cryptography uses features of quantum physics to create encryption keys that are virtually impossible to crack. This technology will enhance data security in 2024.
Cloud Cybersecurity
Cloud security solutions provide scalable and flexible tools for data protection. They include monitoring, analytics, and threat detection systems. They provide tools for access control and encryption in cloud environments.
Internet of Things (IoT) Security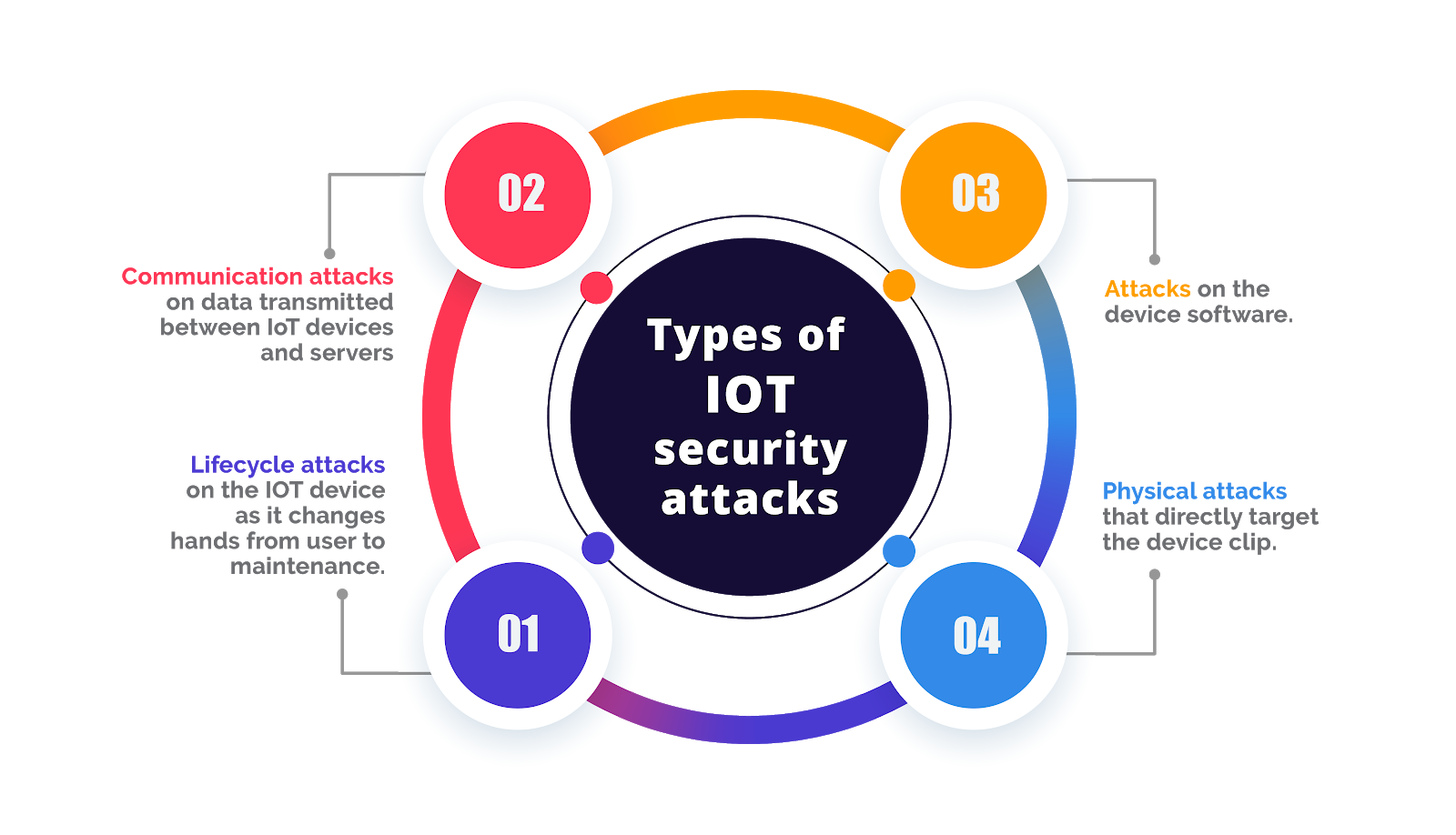
Last year, there was funny news that attackers could attack smart pet feeders due to their lack of built-in security. However, the news seems funny only at first glance. The more digital society becomes, the more at risk we all are. Smart devices have long been used to create botnets and DDoS attacks, and smart speakers, cameras, and TVs, for example, can eavesdrop and spy on you after being hacked. Now imagine the possibilities if attackers hack into a remote employee’s smart speaker and are able to eavesdrop on all work meetings.
Ransomware Resilience, cybersecurity and Mitigation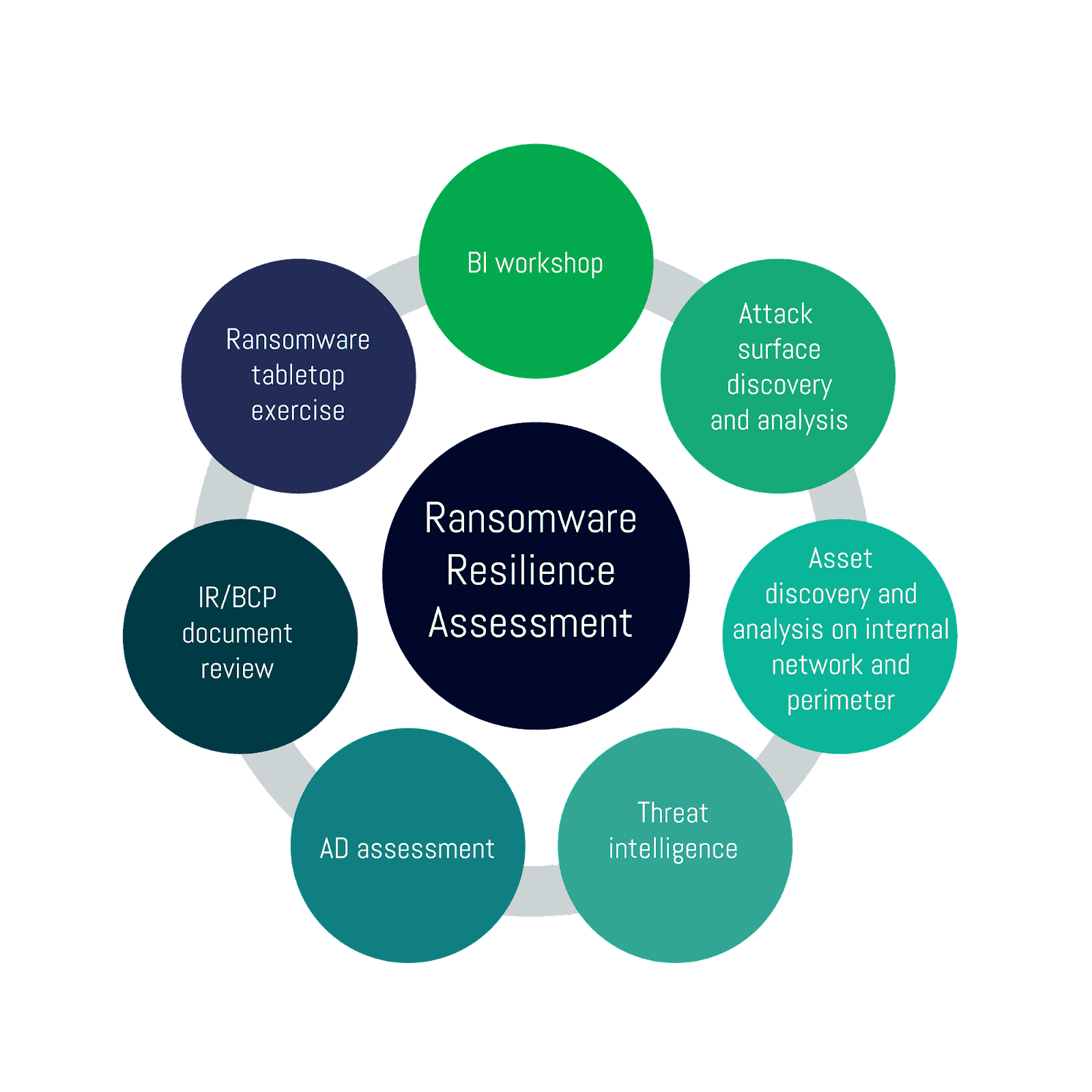
Ransomware resilience and mitigation have become critical focuses in cybersecurity. With the escalating threat of ransomware attacks, organizations prioritize measures to fortify their digital defenses. This includes regular data backups, employee training on cyber hygiene, and advanced threat detection systems for proactive resilience.
Additionally, swift incident response plans, encryption technologies, and a heightened cybersecurity culture contribute to effective mitigation strategies. These efforts not only strengthen an organization’s ability to withstand ransomware but also serve as a deterrent against malicious actors, fostering a more secure digital environment.
Biometric Authentication and Advanced Identity Management
In 2024, more organizations are expected to perform additional identity verification to ensure that all employees, partners, and customers are who they say they are during account registration, especially as artificial intelligence improves.
Organizations will increasingly use identity verification to ensure account access or reset requests. Technology can also compare employee photos and information with government documents, as well as provide fake detection to ensure someone is not using an image or video created by artificial intelligence.
Privacy-Enhancing Technologies for cybersecurity
Privacy-enhancing technologies (PETs) are crucial tools in cybersecurity for safeguarding sensitive information. They use encryption and anonymization to keep data secure during transmission and storage, protecting user identities. PETs are essential for compliance with privacy regulations like GDPR, ensuring responsible data handling. By implementing these technologies, organizations enhance user confidence in engaging with digital platforms, as personal information is shielded from unauthorized access or misuse.
The ongoing development of PETs underscores the commitment to reinforcing digital privacy in an era where data protection is paramount.
Incident Response and Threat Intelligence Sharing
In a cyberattack, an organization’s response should not be limited to its solution. Even if the perpetrators did not achieve their goal, it is important to draw conclusions from the incident and take additional measures like threat intelligence sharing.
Threat intelligence sharing is important in responding to potential threats and should answer several questions. How did the attackers act? What vulnerabilities in the system did they find? Did staff respond adequately to the hack? How effective were the security team’s actions?
Threat intelligence sharing is important for updating security policies and training employees to make the organization more resilient to new cyberattacks. You must learn from others’ mistakes and scrutinize hacking episodes at other companies.
Conclusion
Cybersecurity technologies are becoming increasingly sophisticated and integrated in response to ever-changing threats. With modern developments in artificial intelligence and other technologies featured in this article, companies can build robust and resilient security systems, warning themselves against cyberattacks and keeping valuable data safe. It is important to keep up with new trends and update systems to stay one step ahead of cybercriminals.
BIO:
Stacey Wonder is a content marketer who enjoys sharing best practices for self-development and careers with others. In her free time, Stacey is fond of contemporary dance and classic French movies. You may feel free to reach out to her at GuestpostingNinja@gmail.com or for collaboration suggestions.




