Users may feel well hidden when they are browsing online, but their digital activity is not anonymous at all. Actually, […]
Cybersecurity Basics: Safeguarding Your Personal Information
Every 39 seconds, a cyberattack happens. Now, think about your passwords, bank details, and personal data. How secure do you […]
The Rise of Zero Trust Architecture
Traditional cybersecurity models are starting to show their age. The days when a sturdy firewall and a strong perimeter were […]
What We Can Learn From the CrowdStrike Incident In Terms of Personal Security
The CrowdStrike incident of 2024 sent shockwaves through the cybersecurity world, exposing weaknesses that resonate far beyond corporate walls. The […]
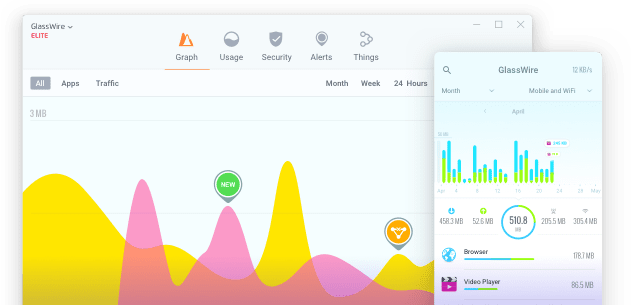
How to Monitor Your Internet Bandwidth Usage: Insights in 2024
Have you ever noticed that your internet connection is playing hide-and-seek game with you? Your video call interrupts at the […]
Traffic Analysis with VPN and Proxy: Ensuring Secure and Efficient Data Flow
Any person sooner or later thinks about how to protect his or her data, hide his or her IP address, […]
BYOD Policies: Crafting Comprehensive Cybersecurity Guidelines for Personal Devices
Employees are increasingly using their personal gadgets for work tasks, pushing many organizations to embrace BYOD policies (Bring Your Own […]
Behind the Screen: The Importance of Transparency in Data Management
Transparency in data management is about as essential as having clear eyesight in today’s digital world. So today, we’re going […]
How to Properly Understand Your Digital Rights and Protections
The digital age has transformed how we access information, communicate, and connect across the globe. However, this rapid advancement brings […]
Navigating Emerging Cyber Threats in 2024
As we step into 2024, the digital landscape continues to evolve at an unprecedented pace. With this rapid advancement comes […]
The New Perimeter: Adapting Cybersecurity for Remote Work
The COVID-19 pandemic has forever changed work culture. Offices sit empty as a record number of people are now working […]
Cybersecurity Horizons 2024: Navigating the Next Wave of Digital Defense
Cybersecurity in the era of digital progress, where data flow is steadily increasing and securing information systems is an issue, […]