Background data usage is the norm for modern computers. But what happens when it gets out of hand?
What is Network Security
As we navigate our personal and professional lives online, ensuring the safety and integrity of our data has become paramount. […]
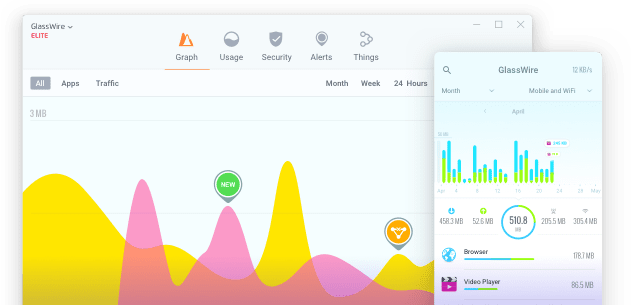
GlassWire Bandwidth Monitoring
With the advent of sophisticated tools like GlassWire’s Bandwidth Usage Monitor, users can bid farewell to bandwidth-related concerns.
GlassWire’s Remote Monitoring
Remote work and IoT devices are more and more common. GlassWire’s Remote Monitoring feature emerges as a powerful ally for comprehensive monitoring.
Cybersecurity Focus: Protect Your Credit Cards Online
Unmasking the Credit Card Stealing Techniques The convenience of online shopping and electronic transactions has soared, but so has the […]
ChatGPT Security Breach
In a concerning turn of events, a significant security breach has occurred with over 100,000 ChatGPT user accounts stolen.
Preventing Ransomware: CISA’s Pre-Ransomware Notifications
CISA’s Early Warning System Offers Critical Defense Against Ransomware Threats Preventing ransomware is a major concern for the vast majority […]
Private Browsing: Is it all it’s cracked up to be?
by Chris Taylor About Chris Taylor: Chris is on the Community Review Board for SANS’s OUCH! (the security awareness newsletter […]
Personal Firewall Explained
You’ve probably heard of personal firewalls if you’re concerned about online security. These software programs are essential tools that act […]
Ferrari data breach – Mar 2023
Ferrari, the renowned Italian luxury sports car manufacturer, recently disclosed that it experienced a data breach after hackers gained unauthorized access to some of the company’s IT systems.
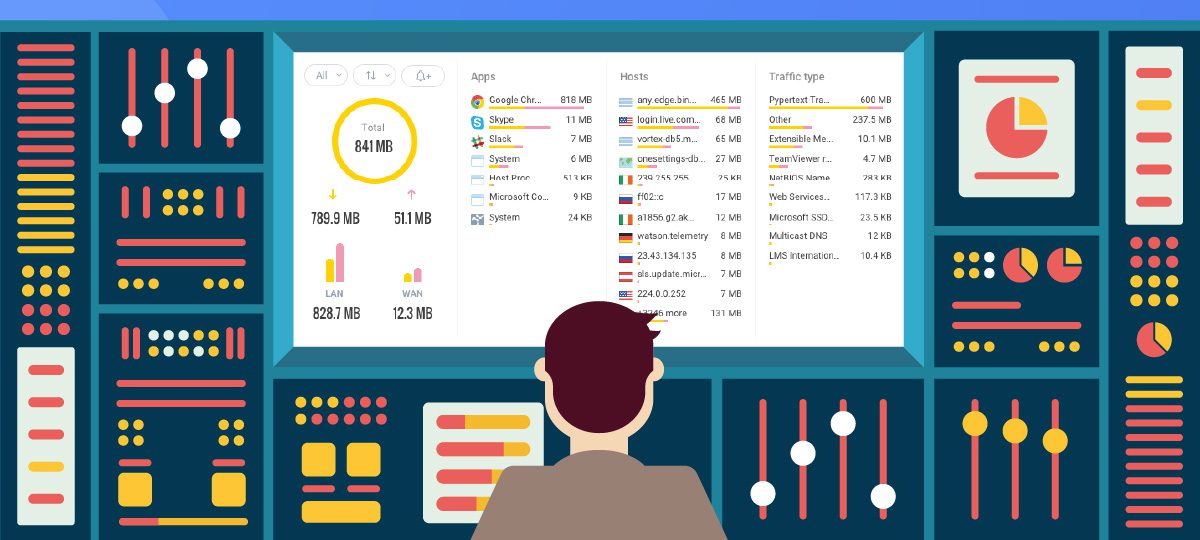
Internet Connection Monitor
With the increasing frequency of cyber attacks, monitoring our internet connection and the data used by various applications has become crucial.
Really, really, deleting files
by Chris Taylor
When you delete a file in Windows, the actual data on disk is not removed. The file is usually moved to the Recycle Bin where it can be easily recovered.