The internet comes with a certain level of risk and it probably goes without saying that using it exposes us to the risks of a spyware.
Many technologies are already monitoring our online activity from pixel trackers and cookies to session tracking.
That’s why when it comes to keeping yourself secure online you should always act as though someone is watching.
We are not alone in what we do online and knowing this you should operate with a certain level of vigilance.
Moving on the non-legit side, the web is also full of several types of malware roaming around eager to jump into your computer, and among them, spyware is certainly the most sneaky and dangerous. You could also easily get one via phishing, so be aware of the emails you open. But…
What really is spyware?
Spyware is a piece of software sneaking into your device and starting running in the background, almost invisibly. While running, it listens to your activity and records relevant information stored on your computers such as personal information, usernames and passwords, payment information, emails, or even the websites you visit and the files you download. Once collected, it silently waits for a trigger to run additional software or share them with a remote computer.
Frequently connected to spyware is identity theft, leading to unwanted access to email clients, social media, and bank accounts. In addition, once into your device, you’ll have a hard time getting rid of it. That’s why it is better to prevent spyware infection to secure your important information.
No matter the device, or the operating system
Historically, the preferred operating system for hackers has been Windows. As a matter of fact, it has been widely used. Windows is still the most used OS all over the world, constituting a very large base of potential victims to look for.
In spite of that, Windows is less popular in richer countries, where Apple man a big share of the market. That’s why since 2017 Mac spyware arose, starting to infect many devices. These viruses are mainly password stealers but could also come in the form of other malware. Popular ones are info stealer or keylogger (read below). They could also disguise themselves by pretending to be a parental control software or a system monitor app.
Your OS may not guarantee the security of your connection, let alone your device type. Mobile are now in the pockets of everyone. Spy apps for mobile are no less widespread and over the years have been reported several cases of mobile spying.
They started rising in number in parallel with the development of mobiles themselves, evolving also in their technology. Mobile spyware affects Android and Apple smartphones with no distinction. They are also particularly devious, as they run in the background. Unfortunately, background applications are not so evident on mobiles as they are on a computer.
They lay in the background undetected and steal sensitive information. Typically, they record phone calls, read SMS and keep track of the user’s activities.
Even worse, once a malware infect your mobile, the software may leverage additional data. These include your GPS location, the image from your camera, or the audio that your microphone records. To deceive you, they use apps recompiled with harmful code and malicious apps posing as legitimate, as well as fake download links.
The way spyware breaches into your smartphone are usually through open wifi connections, flaws in the operating systems, and malicious apps.
There are a few actions you can do to prevent infections and avoid getting spyware on your phone. You’d better connect to trusted networks at home and at work. Keep every software updated, especially the operating system, and avoid third-party apps downloading and installing.
Types of spyware
Spyware come in the form of different software, intended to perform several tasks at once. There is not a unique “spyware” definition. However, the main functionalities of spyware include the following:
Keylogger
Keyloggers’ main function is to record the system activity. Back in the day, they were responsible for keeping track of the pressure of the keys of your keyboard. The software has evolved over the years to the point where it can’t just track the keys you press. They now record the victim’s desktop, monitor the documents sent to a printer, look at websites visited, and even read emails and chats. At this point the attacker get this information, to use at his disposal.
Bank trojans
If general keyloggers collect information with no distinction, bank trojans are specifically designed to infect computers and gather credentials for banks and financial institutions. Acting mainly on the web, so in your browser, they can use the retrieved information to place bank transfers and steal money.
Infostealers
Less specific but equally harmful, infostealers seek information out from the infected device, looking for any file or piece of information the author of the virus may consider useful. They could virtually be anything, from system information to documents, from email addresses to media files and even personal data. They usually exploit browser vulnerabilities to enter your computer, do their job, and send the loot to the attacker.
Password stealers
These applications are typically designed to exploit your system by looking for passwords. No matter if you store them in a password manager software, in your browser, or in a spreadsheet file, their unique job is to find them. Once retrieved, they will send them over to the attacker, opening a range of critical scenarios.
Protect your computer from malicious software and spyware
Prevention always wins over repair. That’s why it is so important to understand which are the main channels for infection and how to avoid getting a virus.
Phishing & spoofing
Phishing has been a major threat over the last few years. Pretending to present you with the login interface of well-known software and making you download malware or type in your credentials, phishing attacks are often the medium of infection for many viruses, spyware included. Phishing is usually paired with spoofing. Spoofing refers to the disguise of an email sender to appear to be from an individual or an organization you trust.
Bundleware
Bundleware is an infection based on the multiple downloads and installations of software. Usually, you apply for a free trial and just want to download and install a single software but by accepting all the terms of service from the provider you end up with several add-ons and plugins installed on your device. Install software only from trusted sources, and avoid third-party or unknown sources.
Backdoors, trapdoors, and other security vulnerabilities
Developers generally use backdoors (known also as trapdoors) as methods to easily bypass the authentication and run debugging. Occasionally, cybercriminals may exploit them to enter a system and take control. Other than being just mistakes, backdoors may be the results of the action of separate software, installed on purpose by a third-party malware (via a trojan or a phishing attack). That’s the case of Back Orifice, one of the most famous backdoor installers and widely exploited by attackers all over the world.
There are very few actions you can do as a user if a software contains backdoors in its code. Usually, similar vulnerabilities are fixed as soon as they are discovered and reported. The only advice we can provide here is to keep your software up to date.
Misleading communication and trojans
As one of the oldest ways to deceive the perception, selling something for what is not is evergreen in frauds. That’s why spyware is never presented for what they are but for everything that could look appealing or useful.
A good example is malware presented as utility software on a malicious website. It pretends to speed up your device, clean your disk or even repair your system from catastrophic errors.
Protect your computer from spyware
If you’ve got a malware infection or specifically a spyware on your computer, don’t despair, it’s not too late.
There are a lot of malware scanner software and malware removal tools that can just get rid of them in a few clicks.
A spyware detector, usually combined with a spyware remover, may be enough to detect spyware in your pc and get rid of the unwanted virus but if it’s not, you’d best access all your critical accounts (bank, email, social networks) and change all the passwords from a different device. That should add an additional layer of protection while preventing the malware from recording the new passwords.
As expected, things may also be not that simple and the detection and removal of spyware could be harder.
Spyware are usually quite complex to find, as they are designed to hide and run in the background.
Modern browsers are quite secure and don’t let web applications dump files into your computer without your consent. Infections are usually a consequence of some human actions, like allowing a download or installing a component. That’s why it is so important to adopt a critical surfing behavior.
For example, how many of you hover with your mouse to check the link you are about to click, before actually clicking?
That’s a best practice that lets you spot unwanted destinations before getting into trouble.
Another good piece of advice is on emails. Always check the email address of the sender.
Quite often phishing attempts make use of email addresses that look almost like the ones they are supposed to be, but with little typos, punctuation signs here and there, and other small differences that should give you a heads up.
You should always handle e-mails from unknown with suspicious eyes.
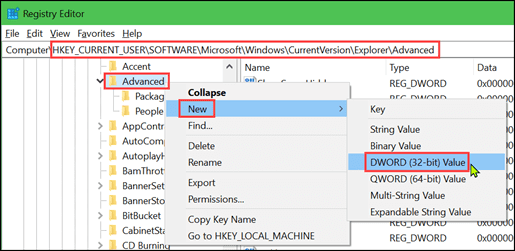
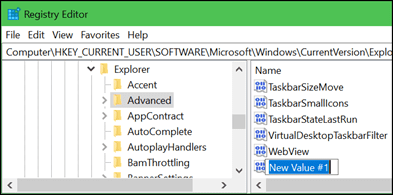
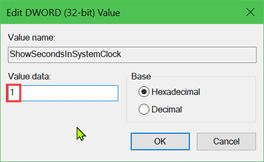
Monitoring the activity of your computer is also a good method of prevention.
GlassWire is a free network monitoring and security tool with a built-in firewall that can easily increase the security of your device with a few clicks.
At GlassWire, we provide a useful tool to keep track of the volume of data exchanged by the software running on your computer, so anyone can simply check for suspicious peaks in data exchange and block the responsible app if this is the case.