Should you be paying closer attention to your home network usage? If you’re like most people, you use WiFi without a second thought. Unless you’re experiencing an outage, you probably don’t care about what’s happening behind the scenes and most probably you don’t check your WiFi usage.
But maybe you should. Wi-Fi monitoring isn’t just for companies. Our world is more connected than ever, and technology safety is a must.
Good network monitoring can help you avoid becoming a victim of financial crimes or identity theft. It reduces the likelihood of hacks and keeps your kids’ personal info secure. If you work from home, then reviewing your usage regularly might even help you appeal to employers. Here’s why your home network deserves a bit more scrutiny — and how to check your usage.
Why Check Data Usage on a WiFi Router?
You may not realize it, but checking your WiFi traffic is a good habit. This applies even if your internet service provider (ISP) doesn’t charge based on usage. Getting familiar with your habits keeps you informed.
Why does it matter? Well, imagine you had a good idea of how much data you used while streaming movies. If you noticed your usage skyrocketing one day, something might be wrong.
One of the biggest problems with security threats is that they often go unseen. For instance, if someone swiped your login credentials, you might not know about it right away. Instead, they could install a backdoor or other program on your computer. The program would then sit around, quietly collecting data until the hacker had enough info to do real harm.
This isn’t a rare scenario. Many types of network exploits and vulnerabilities use similar methods. By running in the background, viruses and backdoors can escape notice until it’s too late. This works to the hacker’s advantage because they can steal as much info as possible.
Understanding how much data you use isn’t a perfect defense, but it’s a start. Suspicious uploads and downloads you didn’t initiate are common hallmarks of active threats. But unless you know what your normal data usage is like, they’re very hard to notice.
How To Check My Wi-Fi Usage with GlassWire?
Many operating systems include built-in traffic monitors. You can also install third-party desktop network traffic widgets. These tools show you how much data you’re currently uploading or downloading. The big issue is that they don’t keep running records. Instead, they’re often limited to displaying short time frames, like the last ten minutes.
The other problem is that generic monitoring apps don’t always show the right level of detail. It’s either too little or too much. For instance, they can tell you at a glance how much data you’re downloading and uploading in total. But this only gives you a general picture of what’s going on. Others reveal which programs are using the network, but they can be overwhelming.
What is GlassWire?
The good news is that there are alternatives. GlassWire is a special tool that focuses on network monitoring and security. Make no mistake: this application revolves around safety. It hits the sweet spot of keeping you connected to relevant info.
GlassWire’s core promise is that it protects your computer in a way anyone can understand. Even though it helps you stay safe from malware, data leaks, and other security threats, it’s easy to use.
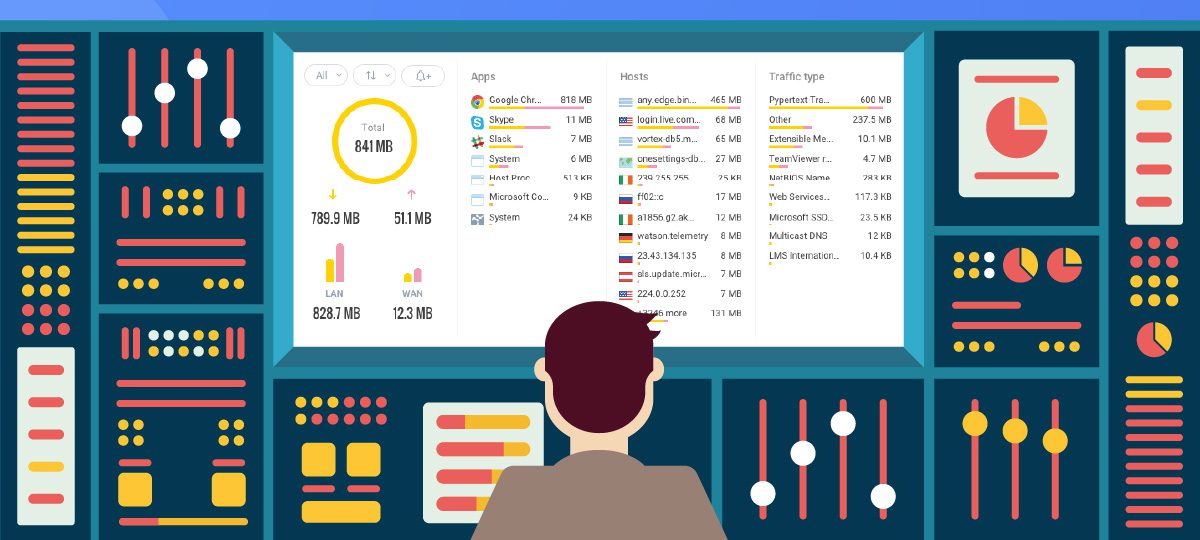
Unlike other tools, you don’t need an IT degree to make the most of GlassWire. The dashboard lays everything out in clear terms, so you can see:
- Which apps are connecting to the internet,
- Where apps connect to including the hostname and country when available,
- Past and present network activity sorted by app, time frame, or host,
- Device-level monitoring (no more neighbors hijacking your WiFi!), and
- How much data each app uses.
GlassWire’s accessibility simplifies monitoring by giving you a straightforward numeric security score. Not only you can check your WiFi usage, you also get to stay informed via desktop widgets and convenient graph layouts. These features are very helpful if you lack IT experience.
Providing real-time visibility into all your network activity is only the beginning. This is why GlassWire helps you take action to stop problems in their tracks. For instance, it can detect anomalies in your traffic and alert you based on your settings. You can also use the lock-down mode to block all network traffic or set up custom firewall profiles within the app.
Conclusion
WiFi traffic monitoring is a vital necessity in the modern connected age. You have plenty of options when it comes to WiFi monitoring. There’s no excuse for neglecting this critical task.
Of course, it’s easier to keep up when you use tools that make the job convenient. GlassWire’s ease of use and broad features make it the perfect candidate for no-fuss monitoring.
Want to understand your home network without feeling like you’re putting in extra work?
Take GlassWire for a free test drive today.